- NFOHump: Offers up-to-date .NFO files and reviews on the latest pirate software releases.
- Hack Forums: Emphasis on white hat, with categories for hacking, coding and computer security.
- Black Hat: The Black Hat Briefings have become the biggest and the most important security conference series in the world by sticking to our core value: serving the information security community by delivering timely, actionable security information in a friendly, vendor-neutral environment.
- Phrack Magazine: Digital hacking magazine.
- Offensive Security Training: Developers of Kali Linux and Exploit DB, and the creators of the Metasploit Unleashed and Penetration Testing with Kali Linux course.
- HackRead: HackRead is a News Platform that centers on InfoSec, Cyber Crime, Privacy, Surveillance, and Hacking News with full-scale reviews on Social Media Platforms.
- Exploit DB: An archive of exploits and vulnerable software by Offensive Security. The site collects exploits from submissions and mailing lists and concentrates them in a single database.
- SecurityFocus: Provides security information to all members of the security community, from end users, security hobbyists and network administrators to security consultants, IT Managers, CIOs and CSOs.
- Hakin9: E-magazine offering in-depth looks at both attack and defense techniques and concentrates on difficult technical issues.
- Metasploit: Find security issues, verify vulnerability mitigations & manage security assessments with Metasploit. Get the worlds best penetration testing software now.
- DEFCON: Information about the largest annual hacker convention in the US, including past speeches, video, archives, and updates on the next upcoming show as well as links and other details.
- Packet Storm: Information Security Services, News, Files, Tools, Exploits, Advisories and Whitepapers.
- The Hacker News: The Hacker News — most trusted and widely-acknowledged online cyber security news magazine with in-depth technical coverage for cybersecurity.
- Hacked Gadgets: A resource for DIY project documentation as well as general gadget and technology news.
- SecTools.Org: List of 75 security tools based on a 2003 vote by hackers.
- KitPloit: Leading source of Security Tools, Hacking Tools, CyberSecurity and Network Security.
Tuesday, June 30, 2020
Ethical hacking : Top 16 best websites to learn hacking
Thursday, June 11, 2020
DOWNLOAD XSSTRIKE – ADVANCED XSS EXPLOITATION SUITE
XSSTRIKE – ADVANCED XSS EXPLOITATION SUITE
XSStrike is really advanced XSS exploitation and detection suite, which contains a very powerful XSS fuzzer and provides no false positive results using fuzzy matching. XSStrike is the first XSS scanner that generates its own payloads. Download xsstrike and test it out.
It also has built in an artificial intelligent enough to detect and break out of various contexts.
FEATURES:
- Powerful Fuzzing Engine
- Context Breaking Intelligence
- AI Payload Generation
- GET & POST Methods Support
- Cookie Support
- WAF Fingerprinting
- Handcrafted Payloads to Filter and WAF Evasion
- Hidden Parameter Discovery
- Accurate Results
DOWNLOAD XSSTRIKE – ADVANCED XSS EXPLOITATION SUITE
Click here to download xsstrike.
What Is Keylogger? Uses Of Keylogger In Hacking ?
What is keylogger?
How does hacker use keylogger to hack social media account and steal important data for money extortion and many uses of keylogger ?
Types of keylogger?
===================
Keylogger is a tool that hacker use to monitor and record the keystroke you made on your keyboard. Keylogger is the action of recording the keys struck on a keyboard and it has capability to record every keystroke made on that system as well as monitor screen recording also. This is the oldest forms of malware.
Sometimes it is called a keystroke logger or system monitor is a type of surveillance technology used to monitor and record each keystroke type a specific computer's keyboard. It is also available for use on smartphones such as Apple,I-phone and Android devices.
A keylogger can record instant messages,email and capture any information you type at any time using your keyboard,including usernames password of your social media ac and personal identifying pin etc thats the reason some hacker use it to hack social media account for money extortion.
======================
Use of keylogger are as follows-
1-Employers to observe employee's computer activity.
2-Attacker / Hacker used for hacking some crucial data of any organisation for money extortion.
3-Parental Control is use to supervise their children's internet usage and check to control the browsing history of their child.
4-Criminals use keylogger to steal personal or financial information such as banking details credit card details etc and then which they will sell and earn a good profit.
5-Spouse/Gf tracking-if you are facing this issue that your Spouse or Gf is cheating on you then you can install a keylogger on her cell phone to monitor her activities over the internet whatever you want such as check Whats app, facebook and cell phone texts messages etc .
=====================
Basically there are two types of keylogger either the software or hardware but the most common types of keylogger across both these are as follows-
1-API based keylogger
2-Form Grabbing Based Keylogger
3-Kernal Based Keylogger
4-Acoustic Keylogger ETC .
====================
How to detect keylogger on a system?
An antikeylogger is a piece of software specially designed to detect it on a computer.
Sometype of keylogger are easily detected and removed by the best antivirus software.
You can view the task manager(list of current programs) on a windows PC by Ctrl+Alt+Del to detect it.
Use of any software to perform any illegal activity is a crime, Do at your own risk.
Wednesday, June 10, 2020
Hacking PayPal's Express Checkout
Do you know what is happening in the background when you buy something in an online shop using PayPal?
In this post we will tackle the following problems:
- How can PayPal's API be tested?
- How does PayPal's Express Checkout work? You can find the detailed report here.
- How can we debit more money than authorized?
How PayPal's API can be tested?
PayPal's Sandbox API
PayPal offers a feature called PayPal Sandbox Accounts, which mimics the production API. The basic idea is that a normal user/shop can test the API and make transactions without actually transferring money. This is the perfect tool for developers to test their API integration.Access to all messages
The next question is how to get access to all messages. All browser-related messages can be inspected, intercepted, and modified via BurpSuite. The main problem here is how to get access to the server-to-server exchanged messages: the messages exchanged between PayPal and a shop. In order to solve this problem, we deployed our own shop. For this purpose we used Magento, which already has a PayPal integration.Once we have our own controlled shop, we can enforce Magento to send all request through a proxy.
In the following picture you can see our setup.
 |
| Test suite for analyzing PayPal's API [1] |
In order to capture the traffic between our Magento hhop and PayPal we proceeded as follows:
- We configured Magento to use a proxy running on localhost:8081.
- We connected the proxy port on the virtual machine with our local machine via SSH remote port forwarding by issuing the following command
- We configured BurpSuite running on our local machine to listen on Port 8081 for incoming requests.
Please note that we uses our own, custom Magento shop in order to be able to test Paypal's API.
PayPal's Express Checkout
An overview of the checkout procedure is depicted in the following: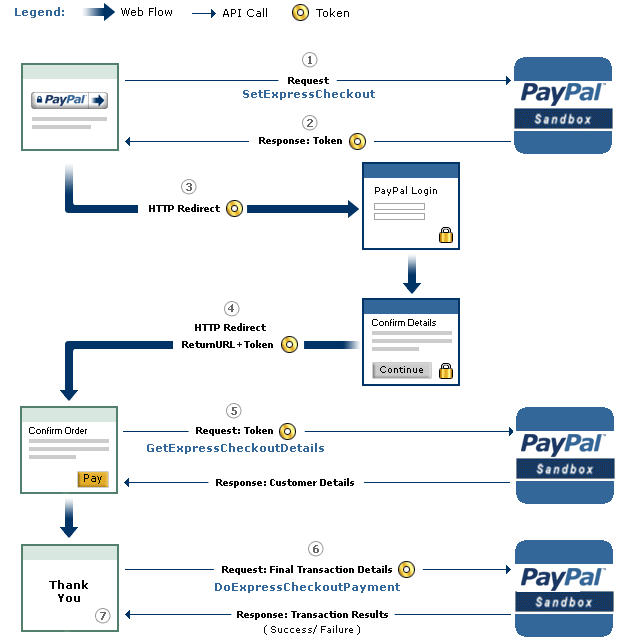 | ||||
| PayPal's Express Checkout [2] |
Step 1: Magento tells the PayPal API where to redirect the user after authorizing the transaction via the parameter RETURNURL and requests a token for this transaction.
Step 2: The PayPal API provides Magento with the token.
Step 3: Magento redirects the user to PayPal's website. The redirect contains the token from the previous step.
Step 4: The user authorizes the transaction. As a result, he will be redirected back to Magento (RETURNURL) with the token.
Step 5: Magento issues a request to the PayPal API to get the transaction details.
Step 6: Magento signals the PayPal API to execute the transaction.
Step 7: Magento serves the success page.
A more detailed view of the protocol and all parameters is shown on page 16 in the full version. We will concentrate only on step 6 and the parameters relevant for the attack.
The Attack
The goal of the attack is to let a shop (in our case Magento) debit more money than authorized by the PayPal user. The core of the attack is Step 6 -- DoExpressCheckoutPayment. Let's get a deeper look at this message: |
| Magento can raise the authorized amount and debit more money from the user's account |
- The shop sends the token, which was issued in the first step of the protocol and identifies uniquely the transaction through all steps.
- The PayerID referring to the user that authorized the payment.
- The AMT defining the amount, which will be transferred.
- The API Credentials authenticating Magento on PayPal.
- The Version pointing to the release number of the API.
As one can imagine, the core problem we found was the change of the AMT parameter. This value can be freely chosen by the shop, despite the fact that the user has authorized a different amount.
We tested only the SandBox API, but refused to test the production API in order to avoid problems. We promptly contacted PayPal's security team and described the problem hoping that PayPal can and will test the production API against the attack.
The response of PayPal can be summarized as follows:
- We don't get any BugBounty since we only tested the Sanbox API. (Fair enough)
- In the Production API PayPal this flexibility is a wanted feature. Thus, PayPal allows a merchant to charge for shipping and/or other expenses different amounts. Any malicious behavior can be detected by PayPal. In case of fraudulent charges the consumer are protected by the Buyer Protection policy.
Authors of this Post
Daniel HirschbergerVladislav Mladenov
Christian Mainka (@CheariX)
[1] BurpSuite Logo
[2] PayPal Express Checkout
Related posts
The OWASP Foundation Has Selected The Technical Writer For Google Season Of Docs
The OWASP Foundation has selected the technical writer for Google Season of Docs by Fabio Cerullo
The OWASP Foundation has been accepted as the organization for the Google Seasons of Docs, a project whose goals are to give technical writers an opportunity to gain experience in contributing to open source projects and to give open-source projects an opportunity to engage the technical writing community.
During the program, technical writers spend a few months working closely with an open-source community. They bring their technical writing expertise to the project's documentation, and at the same time learn about open source and new technologies.
The open-source projects work with the technical writers to improve the project's documentation and processes. Together they may choose to build a new documentation set, or redesign the existing docs, or improve and document the open-source community's contribution procedures and onboarding experience. Together, we raise public awareness of open source docs, of technical writing, and of how we can work together to the benefit of the global open source community.
After a careful review and selection process, the OWASP Foundation has picked the primary technical writer who will work along the OWASP ZAP Team for the next 3 months to create the API documentation of this flagship project.
Congratulations to Nirojan Selvanathan!
Please refer to the linked document where you could look at the deliverables and work execution plan.
Related articles
Monday, June 8, 2020
Gridcoin - The Good
In this post we will take an in depth look at the cryptocurrency Gridcoin, we show how we found two critical design vulnerabilities and how we fixed them.
In the last past years we saw many scientific publications about cryptocurrencies. Some focused on theoretical parts [Source] and some on practical attacks against specific well-known cryptocurrencies, like Bitcoin [Source]. But in general there is a lack of practical research against alternative coins. Or did you know that there are currently over 830 currencies listed online? So we asked ourselves how secure are these currencies, and if they are not just re-branded forks of the Bitcoin source code?
Background
Gridcoin is an Altcoin, which is in active development since 2013. It claims to provide a high sustainability, as it has very low energy requirements in comparison to Bitcoin. It rewards users for contributing computation power to scientific projects, published on the BOINC project platform. Although Gridcoin is not as widespread as Bitcoin, its draft is very appealing as it attempts to eliminate Bitcoin's core problems. It possesses a market capitalization of $13,719,142 (2017/08/10).
Berkeley Open Infrastructure for Network Computing
To solve general scientific meaningful problems, Gridcoin draws on the well-known Berkeley Open Infrastructure for Network Computing (BOINC). It is a software platform for volunteer computing, initially released in 2002 and developed by the University of California, Berkeley. It is an open source software licensed under the GNU Lesser General Public License. The platform enables professionals in need for computation power to distribute their tasks to volunteers. Nowadays it is widely used by researchers with limited resources to solve scientific problems, for example, healing cancer, investigate global warming, finding extraterrestrial intelligence in radio signals and finding larger prime numbers.When launching a BOINC project, its maintainer is required to set up his own BOINC server. Project volunteers may then create accounts (by submitting a username, a password and an email address) and work on specific project tasks, called workunits. The volunteers can process the project tasks and transfer their solutions with a BOINC client.
BOINC architecture
BOINC uses a client-server architecture to achieve its rich feature set. The server component handles the client requests for workunits and the problem solutions uploaded by the clients. The solutions are validated and assimilated by the server component. All workunits are created by the server component and each workunit represents a chunk of a scientific problem which is encapsulated into an application. This application consists of one or multiple in-/output files, containing binary or ASCII encoded parameters.BOINC terminology
- iCPID
- The BOINC project server creates the internal Cross Project Identifier (iCPID) as a 16 byte long random value during account creation. This value is stored by the client and server. From this time on, the iCPID is included in every request and response between client and server
- eCPID
- The external Cross Project Identifier (eCPID) serves the purpose of identifying a volunteer across different BOINC projects without revealing the corresponding email address. It is computed by applying the cryptographic hash function MD5 to (iCPID,email) and thus has a length of 16 byte [Source].
eCPID = MD5(iCPID||email)
- Credits
- BOINC credits are generated whenever a host submits a solution to an assigned task. They are measured in Cobblestone, whereas one Cobblestone is equivalent to 1/200 of CPU time on a reference machine with 1,000 mega floating point operation per seconds [Source]
- Total Credit
- Total number of Cubblestones a user invested with his machines for scientific computations
- Recent Average Credit (RAC)
Gridcoin
As a fork of Litecoin, Gridcoin-Research is a blockchain based cryptocurrency and shares many concepts with Bitcoin. While Bitcoin's transaction data structure and concept is used in an unmodified version, Gridcoin-Research utilizes a slightly modified block structure. A Gridcoin-Research block encapsulates a header and body. The header contains needed meta information and the body encloses transactions. Due to the hashPrevBlockHeader field, which contains the hash of the previous block-header, the blocks are linked and form the distributed ledger, the blockchain. Blocks in the blockchain are created by so called minters. Each block stores a list of recent transactions in its body and further metadata in its header. To ensure that all transactions are confirmed in a decisive order, each block-header field contains a reference to the previous one. To regulate the rate in which new blocks are appended to the blockchain and to reward BOINC contribution, Gridcoin-Research implements another concept called Proof-of-Research. Proof-of-Research is a combination of a new overhauled Proof-of-BOINC concept, which was originally designed for Gridcoin-Classic and the improved Proof-of-Stake concept, inspired by alternative cryptocurrencies.Gridcoin terminology
In order to understand the attacks we need to introduce some Gridcoin specific terms.- eCPID
- Identifier value from BOINC used in Gridcoin to identify the researcher.
- CPIDv2
- contains a checksum to prove that the minter is the owner of the used eCPID. We fully describe the content of this field in the last attack section.
- GRCAddress
- contains the payment address of the minter.
- ResearchAge
- is defined as the time span between the creation time of the last Proof-of-Research generated block with the user's eCPID and the time stamp of the last block in the chain measured in days.
- RSAWeight
- estimates the user's Gridcoin gain for the next two weeks, based on the BOINC contribution of the past two weeks.
Proof-of-Stake
Proof-of-Stake is a Proof-of-Work replacement, which was first utilized by the cryptocurrency Peercoin in 2012. This alternative concept was developed to showcase a working Bitcoin related currency with low power consumption. Therefore, the block generation process has been overhauled. To create a new valid block for the Gridcoin blockchain the following inequality have to be satisfied:
The kernel value represents the concatenation of the parameters listed in Table 2. The referenced unspent transaction output (UTXO) must be at least 16 hours old. The so called RSAWeight is an input value to the kernel computation, it's indicates the average BOINC work, done by a Gridcoin minter.
In direct comparison to Bitcoin's Proof-of-Work concept, it is notable that the hash of the previous block-header is not part of the kernel. Consequently, it is theoretically possible to create a block at any previous point in time in the past. To prevent this, Gridcoin-Research creates fixed interval checkpoint blocks. Once a checkpoint block is synchronized with the network, blocks with older time stamps became invalid. Considering the nature of the used kernel fields, a client with only one UTXO is able to perform a hash calculation each time nTime is updated. This occurs every second, as nTime is a UNIX time stamp. To be able to change the txPrev fields and thereby increase his hash rate, he needs to gain more UTXO by purchasing coins. Note that high UTXO and RSAWeight values mitigate the difficulty of the cryptographic puzzle, which increase the chance of finding a valid kernel. RSAWeight was explained above. Once a sufficient kernel has been found, the referenced UTXO is spent in a transaction to the creator of the block and included in the generated block. This consumes the old UTXO and generates a new one with the age of zero.
The Gridcoin-Research concept does not require much electrical power, because the maximum hash rate of an entity is limited by its owned amount of UTXOs with suitable age.
SHA256(SHA256(kernel)) < Target * UTXO Value + RSAWeight
The kernel value represents the concatenation of the parameters listed in Table 2. The referenced unspent transaction output (UTXO) must be at least 16 hours old. The so called RSAWeight is an input value to the kernel computation, it's indicates the average BOINC work, done by a Gridcoin minter.
In direct comparison to Bitcoin's Proof-of-Work concept, it is notable that the hash of the previous block-header is not part of the kernel. Consequently, it is theoretically possible to create a block at any previous point in time in the past. To prevent this, Gridcoin-Research creates fixed interval checkpoint blocks. Once a checkpoint block is synchronized with the network, blocks with older time stamps became invalid. Considering the nature of the used kernel fields, a client with only one UTXO is able to perform a hash calculation each time nTime is updated. This occurs every second, as nTime is a UNIX time stamp. To be able to change the txPrev fields and thereby increase his hash rate, he needs to gain more UTXO by purchasing coins. Note that high UTXO and RSAWeight values mitigate the difficulty of the cryptographic puzzle, which increase the chance of finding a valid kernel. RSAWeight was explained above. Once a sufficient kernel has been found, the referenced UTXO is spent in a transaction to the creator of the block and included in the generated block. This consumes the old UTXO and generates a new one with the age of zero.
The Gridcoin-Research concept does not require much electrical power, because the maximum hash rate of an entity is limited by its owned amount of UTXOs with suitable age.
Proof-of-Research
Minters relying solely on the Proof-of-Stake rewards are called Investors. In addition to Proof-of-Stake, Gridcoin gives minters a possibility to increase their income with Proof-of-Research rewards. The Proof-of-Research concept implemented in Gridcoin-Research allows the minters to highly increase their block reward by utilizing their BOINC Credits. In this case the minter is called a Researcher.
To reward BOINC contribution, relevant BOINC data needs to be stored in each minted block. Therefore, the software uses the BOINCHash data structure, which is encapsulated in the first transaction of each block. The structure encloses the fields listed in Table 6. The minting and verification process is shown in Figure 2 and works as follows:
To reward BOINC contribution, relevant BOINC data needs to be stored in each minted block. Therefore, the software uses the BOINCHash data structure, which is encapsulated in the first transaction of each block. The structure encloses the fields listed in Table 6. The minting and verification process is shown in Figure 2 and works as follows:
- A minter (Researcher) participates in a BOINC project A and performs computational work for it. In return the project server increases the users Total Credit value on the server. The server therefore stores the minter's email address, iCPID, eCPID and RAC.
- Statistical websites contact project server and down-load the statistics for all users from the project server (A).
- After the user earns credits, his RAC increases. Consequently, this eases the finding of a solution for the Proof-of-Stake cryptographic puzzle, and the user can create (mint) a block and broadcast it to the Gridcoin network.
- Another minter (Investor or Researcher) will receive the block and validate it. Therefore, he extracts the values from the BOINCHash data structure inside the block.
- The minter uses the eCPID from the BOINCHash to request the RAC and other needed values from a statistical website and compares them to the data extracted from the BOINCHash structure, in the event that they are equal and the block solves the cryptographic puzzle, the block is accepted.
 |
| Fig. 2: Gridcoin architecture and minting process |
Reward calculation
The total reward for a solved block is called the Subsidy and is computed as the sum of the Proof-of-Research and the Proof-of-Stake reward.
If a minter operates as an Investor (without BOINC contribution), the eCPID is set to the string Investor and all other fields of the BOINCHash are zeroed. An Investor receives only a relatively small Proof-of-Stake reward.Because the Proof-of-Research reward is much higher than its Proof-of-Stake counterpart, contributing to BOINC projects is more worth the effort.
Statistic Website
At the beginning of the blog post, the core concept behind BOINC was described. One functionality is the creation of BOINC Credits for users, who perform computational work for the project server. This increases the competition between BOINC users and therefore has a positive effect on the amount of computational work users commit. Different websites 4 collect credit information of BOINC users from known project servers and present them online. The Gridcoin client compares the RAC and total credit values stored in a new minted block with the values stored on cpid.gridcoin.us:5000/get_user.php?cpid=eCPID where eCPID is the actual value of the researcher. If there are differences, the client declines the block. In short, statistical websites are used as control instance for Gridcoin. It is obvious that gridcoin.us administrators are able to modify values of any user. Thus, they are able to manipulate the amount of Gridcoins a minter gets for his computational work. This is crucial for the trust level and undermines the general decentralized structure of a cryptocurrency.Project Servers
Gridcoin utilizes BOINC projects to outsource meaningful computation tasks from the currency. For many known meaningful problems there exist project servers 5 that validate solutions submitted by users, 6 and decide how many credits the users receive for their solutions. Therefore, the project servers can indirectly control the amount of Gridcoins a minter gets for his minted block via the total credit value. As a result, a Gridcoin user also needs to trust the project administrators. This is very critical since there is no transparency in the credit system of project server. If you want to know why decentralization is not yet an option, see our paper from WOOT'17.Attacks
In addition to the trust a Gridcoin user needs to put into the project server and statistic website administrators, Gridcoin suffers from serious flaws which allows the revelation of minter identities or even stealing coins. Our attacks do not rely on the Gridcoin trust issues and the attacker does not need to be in possession of specific server administrative rights. We assume the following two simple attackers with limited capability sets. The first one, is the blockchain grabber which can download the Gridcoin blockchain from an Internet resource and runs a program on the downloaded data. The second one, the Gridcoin attacker, acts as a normal Gridcoin user, but uses a modified Gridcoin client version, in order to run our attacks.Interestingly, the developer of Gridcoin tried to make the source code analysis somewhat harder, by obfuscating the source code of relevant functions.
 |
| Fig. 3: Obfuscated source code in Gridcoin [Source] |
Grab Gridcoin user email addresses
In order to protect the email addresses of Gridcoin Researchers, neither BOINC project websites nor statistical websites directly include these privacy critical data. The statistical websites only include eCPID entries, which are used to reward Gridcoin Researchers. However, the email addresses are hidden inside the computation of the BOINCHash (cf. Table 1). A BOINCHash is created every time a Researcher mints a new block and includes a CPIDv2 value. The CPIDv2 value contains an obfuscated email address with iCPID and a hash over the previous blockchain block.
By collecting the blockchain data and reversing the obfuscation function (cf. Figure 4 and Figure 7), the attacker gets all email addresses and iCPIDs ever used by Gridcoin Researchers. See the reversed obfuscation function in Figure 4 and Figure 5.
Evaluation
We implemented a deobfuscation function (cf. Figure 7) and executed it on the blockchain. This way, we were able to retrieve all (2709) BOINC email addresses and iCPIDs used by Gridcoin Researchers. This is a serious privacy issue and we address it with our fix (cf. The Fix).Steal Gridcoin users BOINC reward
The previous attack through deobfuscation allows us to retrieve iCPID values and email addresses. Thus, we have all values needed to create a new legitimate eCPID. This is required because the CPIDv2 contains the last block hash and requires a re-computation for every new block it should be used in. We use this fact in the following attack and show how to steal the computational work from another legitimate Gridcoin Researcher by mining a new Gridcoin block with forged BOINC information. Throughout this last part of the post, we assume the Gridcoin Minter attacker model where the attacker has a valid Gridcoin account and can create new blocks. However, the attacker does not perform any BOINC work. |
| Tab. 1: BOINCHash structure as stored and used in the Gridcoin blockchain. |
 |  |
| Fig. 4: Obfuscation function | Fig. 5: Deobfuscation function |
Evaluation
In order to verify our attacks practically, we created two virtual machines (R and A), both running Ubuntu 14.04.3 LTS. The virtual machine R contained a legitimate BOINC and Gridcoin instance. It represented the setup of a normal Gridcoin Researcher. The second machine A contained a modified Gridcoin-Research client 3.5.6.8 version, which tried to steal the Proof-of-Research reward of virtual machine R. Thus, we did not steal reward of other legitimate users. The victim BOINC client was attached to the SETI@home project 11 with the eCPID 9f502770e61fc03d23d8e51adf7c6291.
The victim and the attacker were in possession of Gridcoins, enabling them to stake currency and to create new blocks.
 |
| Fig. 6: CPIDv2 calculation deobfuscated |
Initially both Gridcoin-Research clients retrieved the blockchain from other Gridcoin nodes in the Gridcoin network.
 |
| Fig. 7: Reverse the CPIDv2 calculation to get iCPID and email address |
Once a block had been created and confirmed, the attacker received the increased coin reward with zero BOINC contribution done. The attack could only be detected by its victims because an outside user did not know the legitimate Gridcoin addresses a Researcher uses.
All blocks created with our victim's eCPID are shown in Table 2. Illegitimate blocks are highlighted. We were able to mint multiple illegitimate blocks, and thus stealing Research Age from our victim machine R. All nine blocks created and send by our attacker to the Gridcoin network passed the Gridcoin block verification, were confirmed multiple times, and are part of the current Gridcoin blockchain. During our testing timespan of approximately three weeks, the attacker machine was wrongfully rewarded with 72.4 Proof-of-Research generated Gridcoins, without any BOINC work. The results show that the attack is not only theoretically possible, but also very practical, feasible and effective. The attack results can be reproduced with our Gridcoin-Research-Attack client.
The Fix
In order to fix the security issue, we found one solution which does not require any changes to the BOINC source code nor the infrastructure. It is sufficient to change some parts of the already existing Gridcoin Beacon system. Thus, our solution is backwards compatible.The current Gridcoin client utilizes so called Beacons to register new eCPIDs and stores them as a transaction of 0.0001 Gridcoins in a Superblock which is created every 24 hours. A Beacon encloses the user's personal eCPIDs, a corresponding unused (but irreversible) CPIDv2, and the wallet's main Gridcoin payment address. Once the Superblock is created, the eCPIDs is bound to one Gridcoin payment address. During the block verification process this bond is unfortunately not checked. Furthermore, the existing Beacon system does not use any strong asymmetric cryptography to ensure authenticity and integrity of the broadcasted data. We propose to extend the Beacon system with public key cryptography. In detail, we suggest that a user binds his fresh public key PK_1 to a newly generated eCPID, and then storing them together in a Superblock. An initial Beacon would therefore contain a hashed (e.g. SHA-256) eCPID, the public key, a Nonce, and a cryptographic signature created with the corresponding secret key SK_1 of the public key. This allows only the owner of the secret key to create valid signatures over blocks created with his eCPID. Thus, an adversary first needs to forge a cryptographic signature before he can claim Proof-of-Research work of another Gridcoin user. Thus, he is not capable of stealing the reward of the user.
| Beacon to create a eCPID, public/secret key pair bond |
For verification purposes nodes fetch the corresponding latest public key from one of the Superblocks. Furthermore, this Beacon structure allows a user to replace his previous public key associated with his eCPID. This is realized by submitting a new Beacon with a new public key PK_2, signed with his old secret key.
| Beacon to update a eCPID, public/secret key pair bond |
All Beacons in the chain are verifiable and the latest public key is always authentic. The Nonce provide freshness for the signature input, and therefore prevent replay attacks against the Beacon system.
Note that the eCPID needs to be completely unknown to the network, when sending the initial Beacon, for this concept to work as intended. The hash function ensures, that the Beacon does not reveal the fresh eCPID. As a result, an attacker is unable to mint with a eCPID even if he was able to intercept an initial Beacon and replaced the public key and signature with his own parameters, beforehand. This solution does not require any changes in the BOINC source code or the project servers.
Sign a block
In order to claim the Proof-of-Research reward for a newly created block, the Gridcoin minter computes a signature over the hash of the blockheader. Afterwards, he stores the resulting value at the end of the corresponding block in a new field. The private key used for the signature generation must correspond to the advertised public key by the user. It is important to note that the signature value is not part of the Merkle tree, and thus does not change the blockheader. In the end, the signature can then be verified by every other Gridcoin user via the advertised public key corresponding to the eCPID of the Gridcoin minter.Responsible Disclosure
The attacks and the countermeasures were responsibly disclosed to the Gridcoin developer on the 14th of September, 2016. The developer used our proposed countermeasures and started to implement a new version. Since version 3.5.8.8, which is mandatory for all Gridcoin users, there exists an implementation, which contains countermeasures to our reward stealing attack.See our next blog post, why Gridcoin is still insecure and should not be used anymore.
Further Reading
A more detailed description of Gridcoin and the attacks will be presented at WOOT'17, the paper is available here.
Authors
Tobias Niemann
Juraj Somorovsky
Read more
- Pentest Checklist
- Pentest Practice
- Pentest Tools Framework
- Hacker Code
- Pentest Vs Red Team
- Hacking Youtube
- Pentestbox
- Pentest Partners
- Hacking To The Gate
- Pentest Framework
- Hacking Tools
- What Hacking Is
- Hacking Typer
- How To Pentest A Website With Kali
- Pentest Methodology
- Hacking Meaning
- Pentest Tutorial
- Pentesterlab
- Pentestbox
- Pentest Jobs
November 2019 Connector
*|MC_PREVIEW_TEXT|*
|
|
Subscribe to:
Comments (Atom)










